Key distribution overview
Many of the encryption mechanisms and encryption algorithms discussed above are public, so security does not rely on keeping algorithms secret. Instead, security depends on protecting the keys. As a result, key management is a critical topic. Key management primarily includes key generation, distribution, authentication, and usage.
Symmetric key automatic distribution
One approach for distributing symmetric keys is to establish a key distribution center (KDC). The KDC is an authoritative key distribution service that helps address the growth in the number of keys and the security of shared keys. The KDC issues temporary session keys for communicating users; each session key is valid only for the duration of the session.
For example, in a KDC distribution scenario:
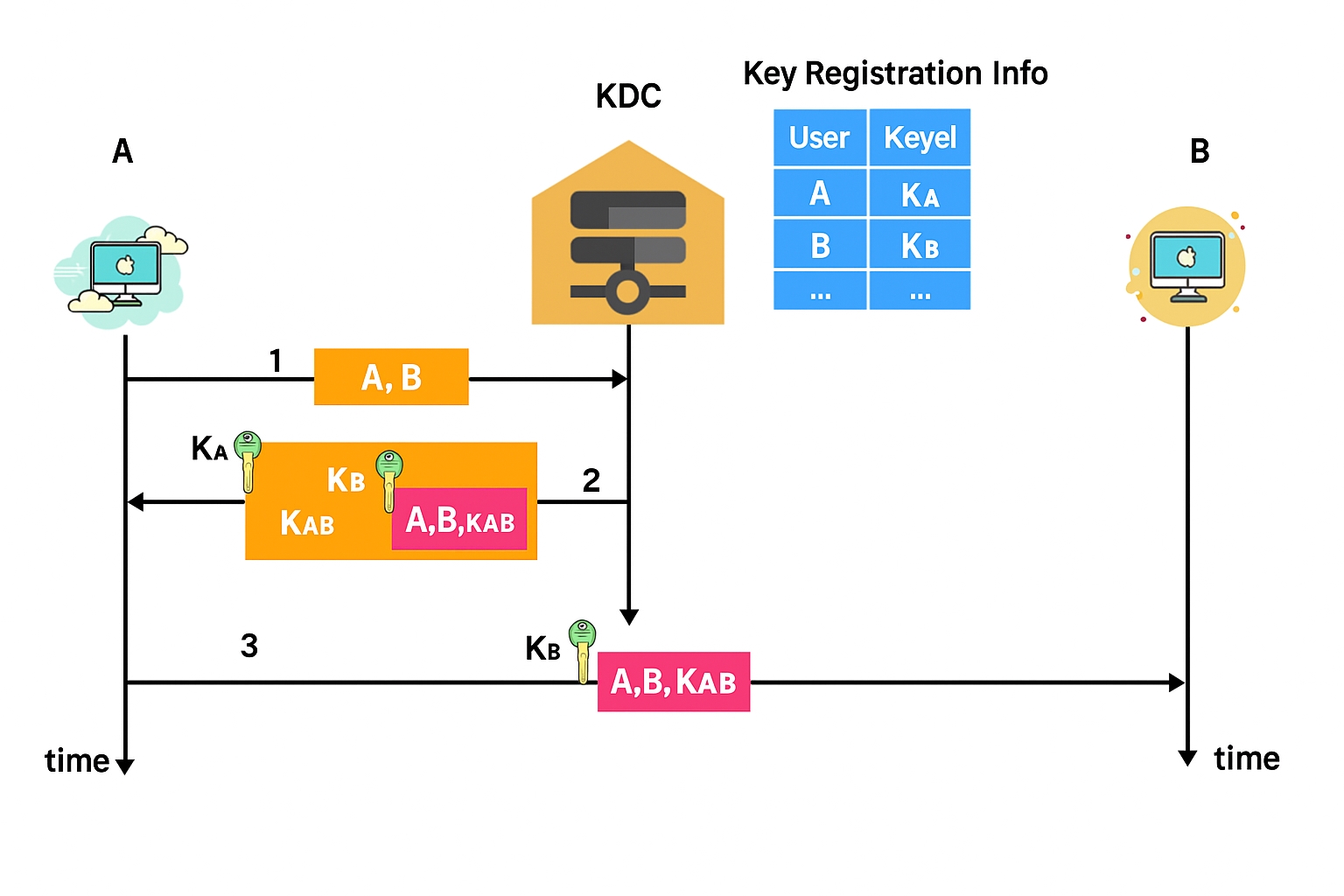
Users A and B are registered with the KDC. When registering, A and B have each installed a master key for communication with the KDC, denoted KA and KB. These are referred to as master keys.
First, A sends a plaintext request to the KDC indicating that A wants to communicate with B. The plaintext includes the registered identities of A and B.
The KDC generates a one-time session key KAB for this session and sends a reply to A. The reply is encrypted with A's master key KA and includes the session key KAB plus a message intended for B that is encrypted under B's master key KB. Because A does not have KB, A cannot read the message intended for B.
A forwards the KB-encrypted message to B. When B receives it, B learns that A wants to communicate and obtains the session key KAB. A and B can then communicate securely using KAB.
A potential concern is an attacker C impersonating A by intercepting the message A sends to B and replaying it. Because C does not know A's master key KA, C cannot obtain KAB from the KDC reply. The KDC can also include timestamps in messages to prevent reuse of previously intercepted messages. In addition, master keys KA and KB should be periodically refreshed.
One well-known key distribution protocol is Kerberos V5, a ticket-based authentication protocol that functions as a KDC and is widely used on the Internet. Kerberos uses AES for encryption. The following describes the simpler Kerberos V4 workflow; V5 follows the same basic principles.
Two Kerberos servers are involved: the Authentication Server (AS) and the Ticket-Granting Server (TGS).
Authentication Server (AS): verifies user credentials and issues Ticket Granting Tickets (TGTs).
Ticket-Granting Server (TGS): validates TGTs and identities, and issues service tickets.
A is the client requesting a service from server B. Kerberos authenticates that the request comes from A and not from an impostor, and then issues a session key for A and B.
A presents its identity in plaintext to the AS. The AS maintains registered identities and corresponding passwords. After verifying A's identity, the AS sends A a message encrypted with A's symmetric key KA. That message contains a session key KS for A and TGS communication, and a ticket for TGS encrypted with the TGS key KTG. When A receives the message, A derives KA from its password and decrypts the AS message to obtain KS and the KTG-encrypted ticket.
A then sends a request to the TGS that includes the KS-encrypted authenticator (such as a timestamp), the KTG-encrypted ticket from AS, and the target service B. The TGS validates the ticket and authenticator, then issues two tickets containing the session key KAB: one encrypted for A using KS, and one encrypted for B using B's key KB.
A forwards the ticket intended for B to B, along with an authenticator encrypted under KAB (for example, a timestamp). B responds by returning the timestamp incremented by one, encrypted with KAB, to confirm receipt. After this exchange, A and B use the session key KAB to communicate securely.
Public key distribution and certification
The main issue in public key distribution is ensuring the authenticity of a public key. Possession of a public key alone does not prove the key belongs to the claimed owner. The authority that certifies public keys is the Certification Authority (CA). A CA issues certificates that contain the public key and identifying information about the holder; these certificates are digitally signed by the CA. Relying parties accept a public key as valid only when presented with a CA-issued certificate.