MICROSAR Network Security Explained
Collection of circuit diagrams and schematics: gallery of detailed electrical diagrams and layout images for engineers and developers.
Collection of circuit diagrams and schematics: gallery of detailed electrical diagrams and layout images for engineers and developers.
Technical analysis of DarkComet RAT: static and dynamic behavior, infection/persistence, keylogging and exfiltration, identified IOCs and remediation steps.
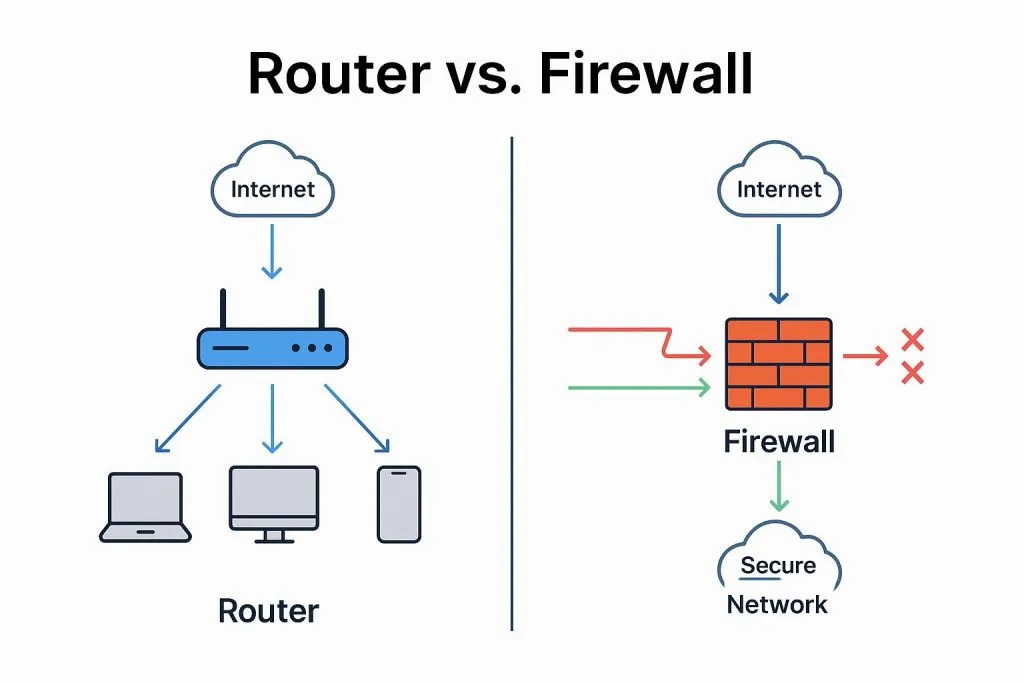
Technical overview of firewall fundamentals covering security zones, security policies, stateful session table behavior, aging and server-map handling for protocol exceptions.
Analysis and reproduction of an authentication and communication vulnerability in Rockwell PLCs: ENIP protocol allows remote IP modification (AB1756), with patch guidance.
ATEEL designations and certifications: EU/UNECE technical service body; ISO/IEC 17020 & 17025 accredited; TISAX; Fusa, cybersecurity, pen and fuzz testing.
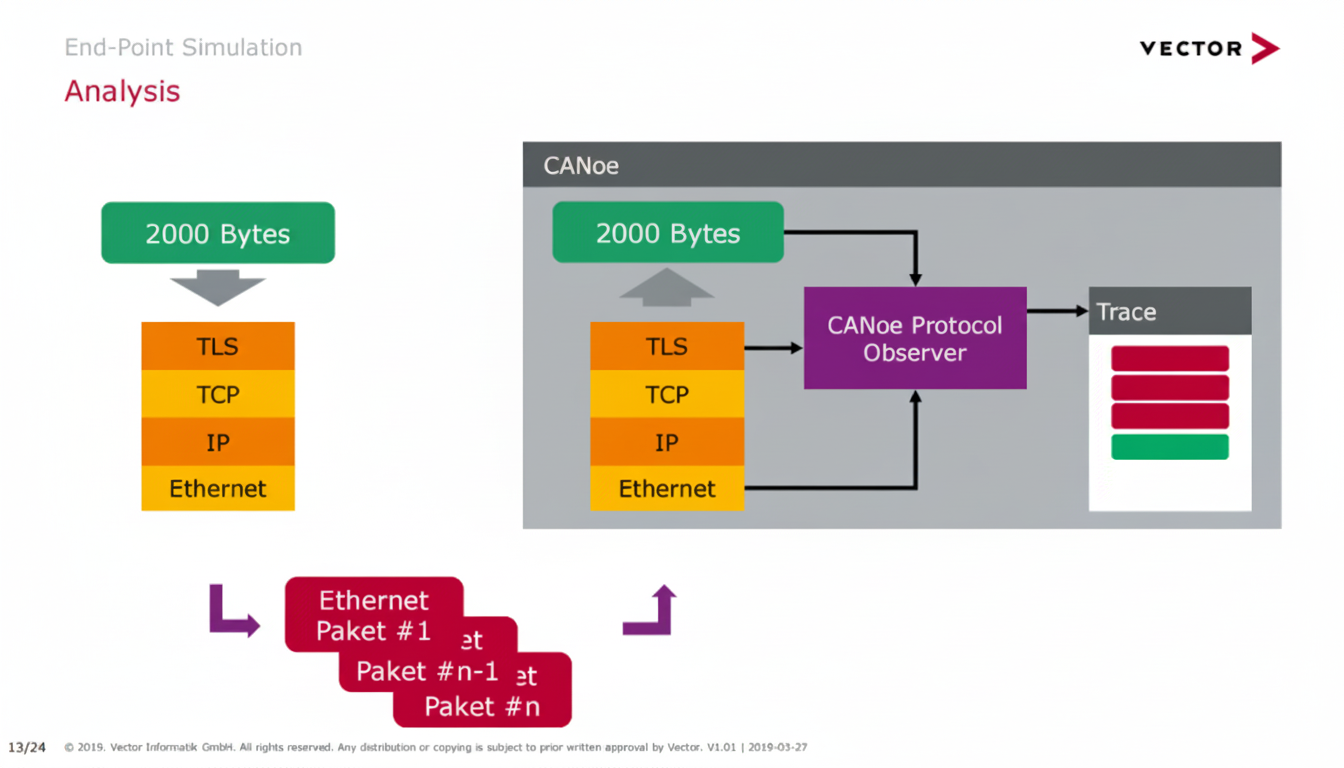
Explains using private certificates to access decrypted messages from vehicle ECUs for application-layer analysis and signal manipulation while leaving ECU security unchanged.
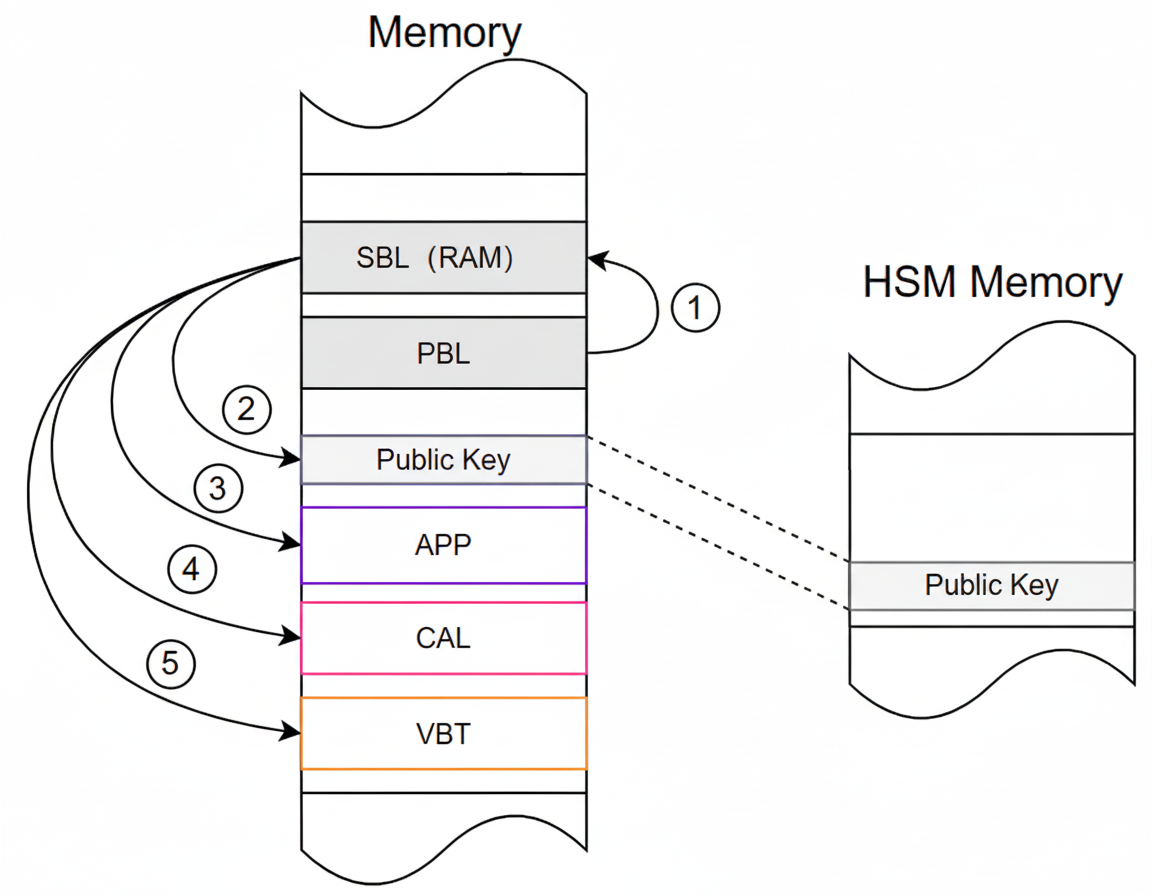
Explains public key roles, storage, and verification in connected vehicles, covering RSA-2048/SHA-256 signatures, VBT root-hash checks, and production-line/OTA key handling.
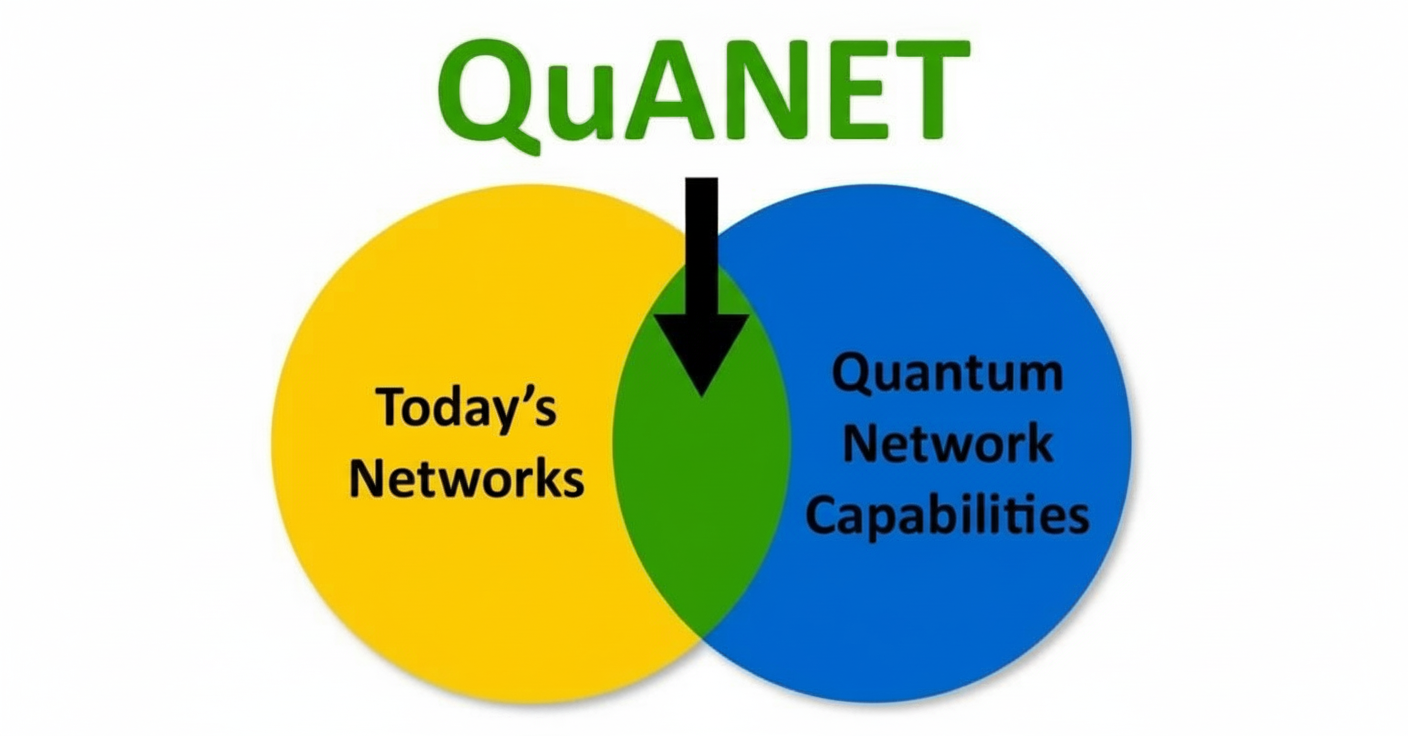
DARPA QuANET outlines a 51-month plan to build hybrid quantum-classical metropolitan networks—developing a ruggedized qNIC, quantum-enhanced protocols TA2/TA3 and metrics
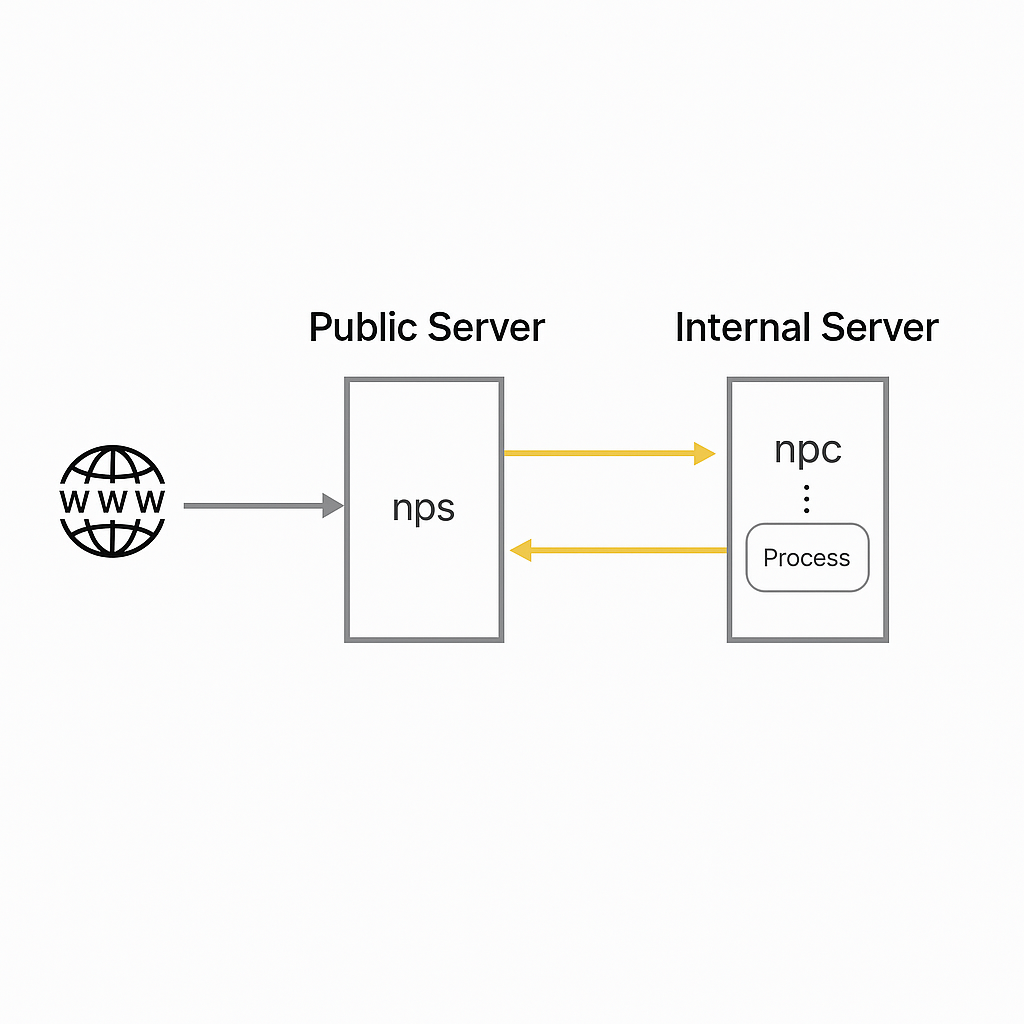
Overview and configuration examples of NAT traversal and reverse proxy tools (nps, frp, EW, ngrok), covering TCP/UDP forwarding, SOCKS5, web UI and deployment.
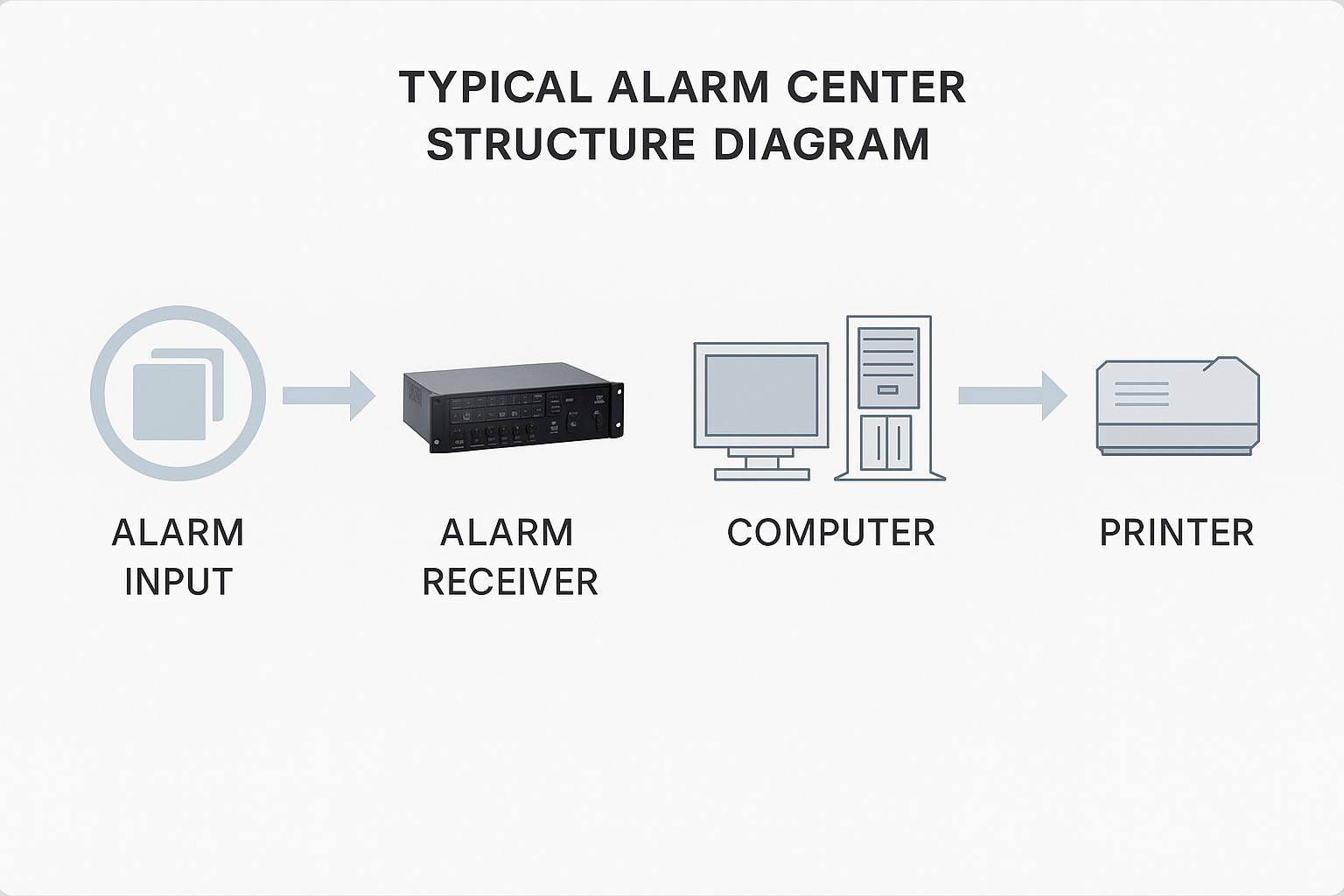
Technical overview of an alarm subsystem architecture, covering front-end sensors, transmission methods (PSTN/IP/GPRS), and video verification.
Guide to white-plus-black technique and DLL hijacking: locating signed 'white' binaries, building replacement DLLs, testing loading, and detection methods for defenders.
Survey of NAT traversal and internal network proxy tools (nps, frp, EW, ngrok), covering architecture, configuration examples, and usage for penetration testing.