Understanding IDS and IPS
Technical overview of intrusion detection and prevention: IDS components, HIDS/NIDS classifications, deployment strategies, IPS inline blocking and relationship with IRS.
Technical overview of intrusion detection and prevention: IDS components, HIDS/NIDS classifications, deployment strategies, IPS inline blocking and relationship with IRS.
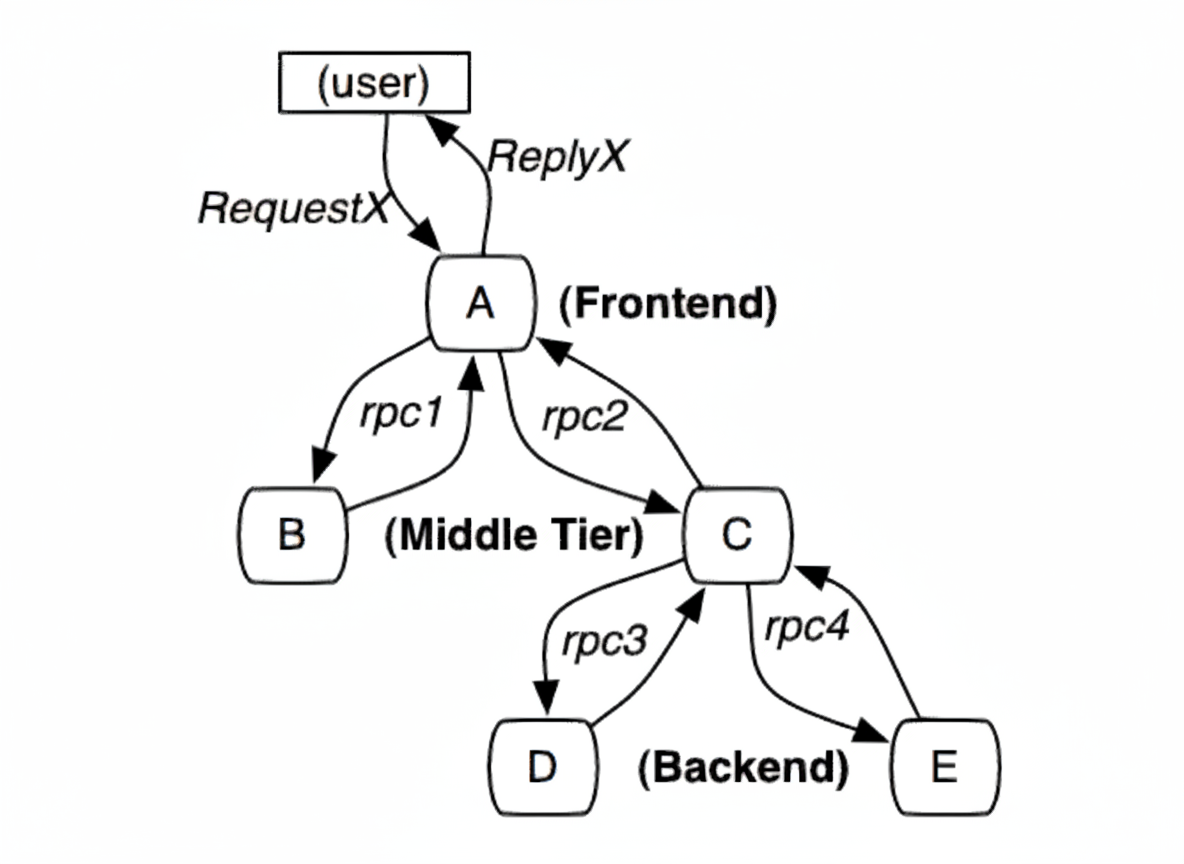
Overview of full-stack tracing and Google Dapper concepts, call-chain instrumentation, collectors, analysis, and comparison of Zipkin, Pinpoint, and SkyWalking.
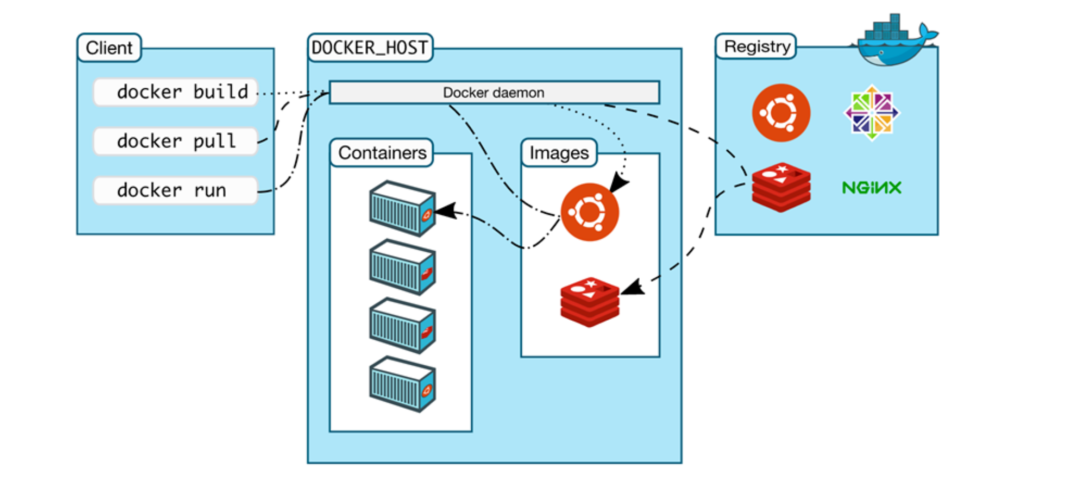
Concise technical overview of cloud computing, deployment and service models, and cloud-native risks, with emphasis on cloud security and Kubernetes misconfigurations and threats.
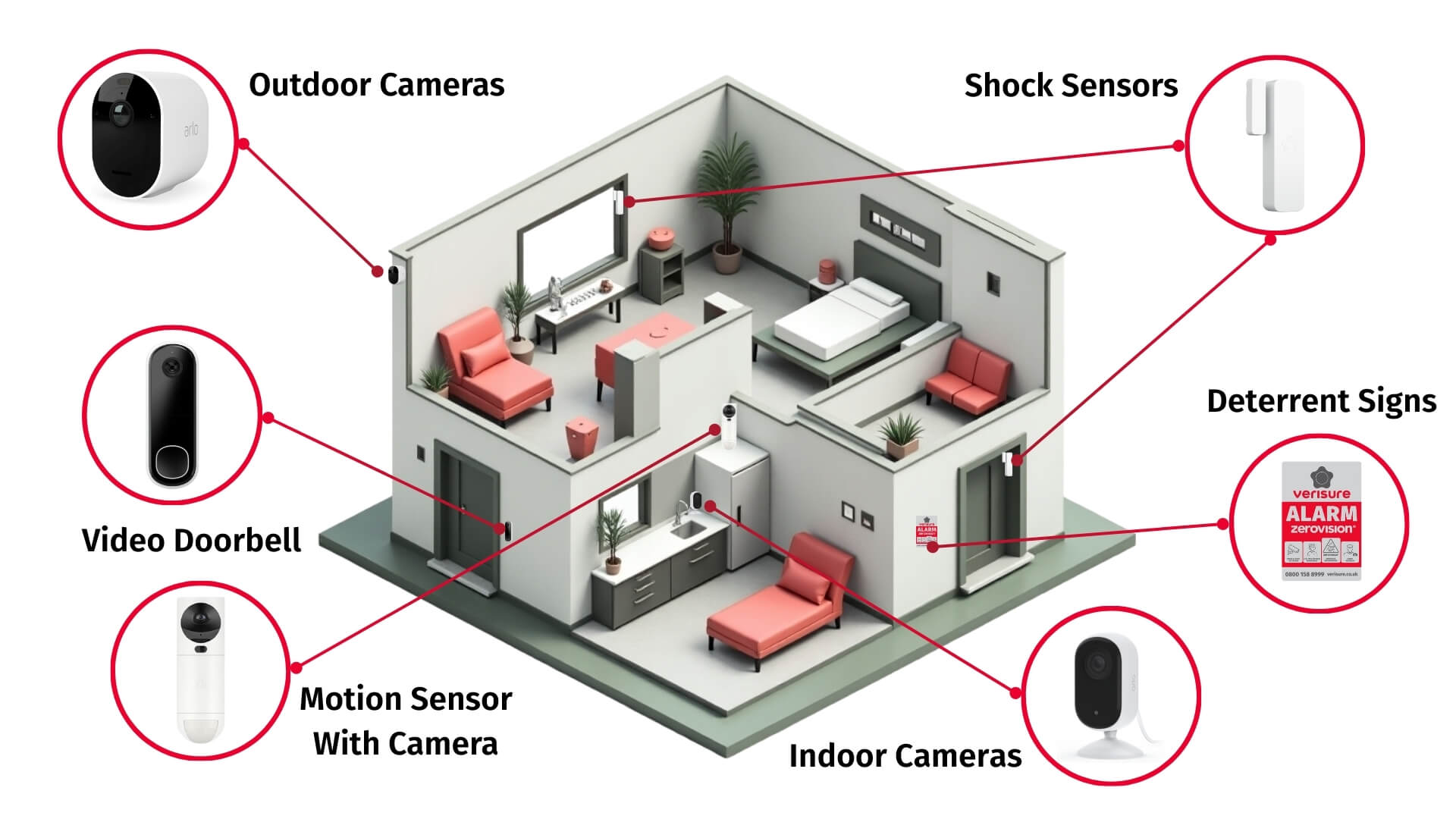
Technical overview of security systems and video management system components: access control, intrusion alarms, intelligent analysis for monitoring, response and evidence.
Summary of five cybersecurity areas—confidentiality, integrity, availability, trust, and risk management—and their role in protecting privacy, assets, and national security.
Structured guide to video surveillance commissioning: preparation, equipment checks, camera and VMS adjustments, alarm linkage verification, and commissioning report requirements.
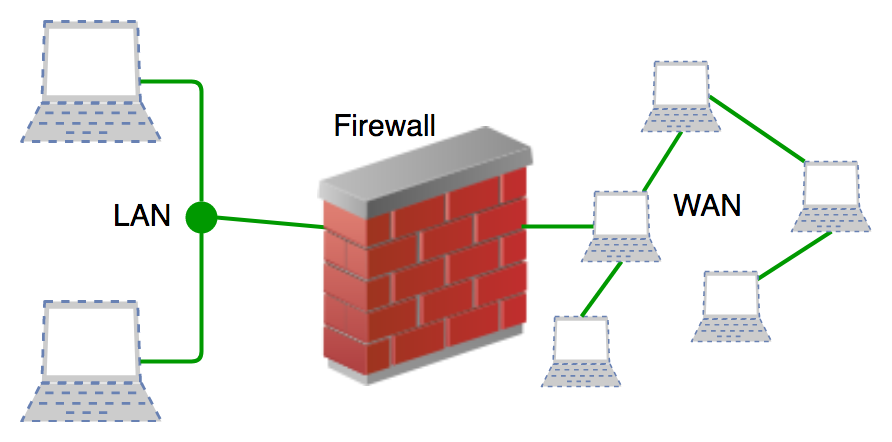
Technical overview of firewalls, their roles, key functions and principal technologies for network security to control access, inspect traffic and log events.
Overview of network monitoring systems, common types (firewall, IDS/IPS, traffic and log analysis, IAM) and required devices with deployment and privacy considerations.
Technical overview of security systems covering surveillance cameras and access control, plus DVR/NVR, alarm integration, remote monitoring, and incident response.
Analysis of rising IoT device attacks on OT networks: risks from legacy devices and default credentials, impact on manufacturing, mitigations: discovery, segmentation, identity.
Review of China's Vehicle Information Security Technical Requirements draft, analyzing cybersecurity implications for plug-and-play, authorization, risk-based scope and management.
Guide to decrypting and decompiling WeChat mini program wxapkg on macOS, capturing traffic, extracting SM2 keys, and testing backend authorization risks.